Domain-Based Message Authentication Reporting and Conformance
Domain-based message authentication reporting and conformance, also known as DMARC, is a set up created by a group of organizations, having the objective to reduce concerns based on email related abuse by implementing and reporting operations including email authentication protocol. As we analyze the recent attacks, spoofing and phishing attacks have increased drastically over the period of time. DMARC was implemented with the objective to provide a solution to these kinds of problems by helping the sender to protect their mail from spoofing. DMARC provides a standard solution for receivers to authenticate the mail received by making use of mechanisms in SPF (Sender Policy Framework) and DKIM (Domain Keys Identified Mail). The number of spam's reaching a normal mail account is considerably high these days. E-commerce and social media are very much responsible for these unwanted mail that flood your account. Emails are very easy to replicate and over the period the perfection in spoofing a mail has increased. It's very difficult to sort between a spoofed mail and genuine mail, which could easily compromise a user. DMARC provides a solution to this kind of problems, considering both sender and receiver issues and authentication problems. Before getting into DMARC, let's review SPF and DKIM for better understanding.
SPF (Sender Policy Framework)
As we know, SPF is a method to reduce email spoofing where the domain of the sender is authenticated for sending mails. It helps the mail server to identify the original domain and reject mail from the fake servers. Simply SPF is a DNS text entry, which has a list of servers that are considered to be legit for sending mail for specific domain. In SPF specification, each domain mentions their respective mail details and the authorized senders. This note is called the SPF record, which is updated in the DNS records. When a mail is received the client searches for the SPF record to determine whether the mail is obtained from a genuine source or not. If the mails are from an authorized domain, then the search provides a pass result and allows the mail or would create a fail result which shows that the mail is from an unauthorized source. Let's understand the working by analyzing the following diagram:

11 courses, 8+ hours of training
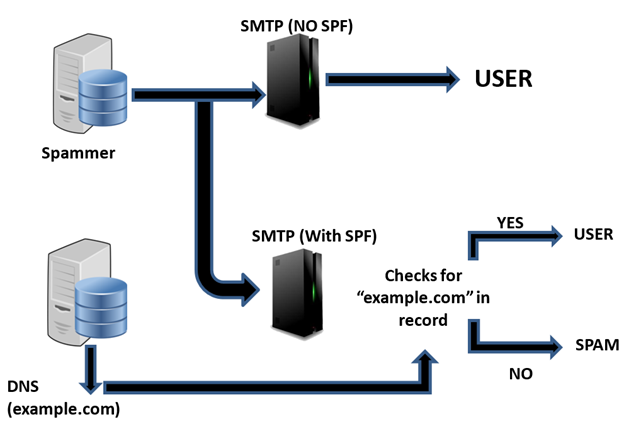
Figure 1: SPF Working
In the above image there are two SMTP servers, first one without SPF and second one with SPF. The one without SPF does not filter the mails; it won't be able to identify weather it's from an authorized server or from a spam server. But in the second server with SPF, the server compares it with the authorized server list setup using SPF and allows the genuine mail to the user end resulting others to a spam folder.
For normal users we can use SPF by adding a SPF record to the DNS. For those who are having a SPF record in the DNS, specify the details of the server in the record as follows, before the last operator:
"include:spf.example.com"
Domain Keys Identified Mail (DKIM)
DKIM allows the sender to include a digital signature to the mail header which is generated by MTA using an algorithm; it creates a unique string of characters with hash value. When these signatures are generated, the public key used to generate them is stored. As the receiver gets the mail, the receiver end MTA verifies the signature with the help of stored public key using DNS. This public key is used to decrypt the signature in the mail header to calculate the hash value added by the sender. These both hash values are compared to check whether the mail has been altered by a third party or not, giving full security to the mail. If the signature doesn't match, a SPAM tag is added to the mail so that the receiver could easily identify them. The following diagram shows the working of DKIM:
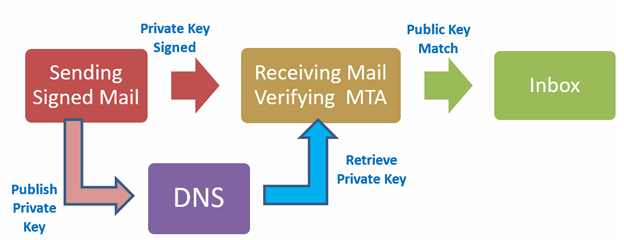
Figure 2: DKIM working
- DKIM Signature is added using the private key to the message and the mail is sent to the receiver.
- After receiving at the receiver MTA the key for decryption is retrieved from the DNS to match the signatures.
- If the mail is tampered, the signatures won't match and will be tagged as Spam.
Testing DKIM in Gmail
As we all know, Gmail is one of the popular mail service used across the globe. For normal users having Gmail account can test the authenticity of their mail easily. Open a received mail and click the down arrow near the reply button. Select "show original" tab which will show the signed server details to verify the signature.
Understanding DMARC
SPF and DKIM could be used against spams and control to unauthorized mail to an extent. But the small disadvantage of the above mentioned service is that, the action that needed to be carried out at the receiver end is not mentioned. Users usually discard, block or delete the mails that are notified by SPF or DKIM protocols or some might add it to their spam list to avoid flooding of their inbox. In this case, there are chances of missing mail due to blocking or marking them as spam. There is nothing a sender can do under such situation to prevent these kind of activities or to increase the efficiency of mail send. DMARC provides a solution to the problems addressed above. The main objective of DMARC is to alert the receiver about the policies in the mail flow and also it gives a feedback to the sender about the mails that are being rejected.
DMARC Working
DMARC working can be explained by a set of steps as shown below:
- Firstly, we need to authenticate the mail using the SPF or DKIM as mentioned earlier. By authenticating the mail, we establish to the ISP that the message being sent is crafted by us.
-
Next step is to add a DMARC record to the DNS, which determines the flow of the message. This can be done by adding a few lines to the records as follows:
_dmarc.test.com IN TXT "v=DMARC1; p=quarantine; rua=mailto:dmarc-report@test.com ruf=mailto: dmarc-report@test.com
By adding the above code to the record, it means that, any mail that fails to authenticate from "test.com" will be sent to spam folder and the reports will be sent to dmarc-report@test.com. For writing the code there are few tags, which are mentioned below:
Table 1: DMARC Tags
Tag Name
Required
Purpose
Sample
v
Required
Protocol version
v=DMARC1
p
Required
Policy for domain
P=quarantine
pct
Optional
% of messages subjected to filtering
pct=20
rua
Optional
Reporting URL of aggregate reports
rua=mailto:dmarc-report@test.com
sp
Optional
Policy for sub domains of the domain
sp=reject
aspf
Optional
Alignment mode for spf
aspf=r
- After adding the TXT record, when a mail is received, the ISP will check to the details mentioned in the DNS record for authentication and will perform the function that we have specified in the DNS record.
- Finally, you can check the mail reports to find out the fake mails that are forwarded to the specified mail address and work on it to solve phishing attacks.
The main point to keep in mind is that, every mail coming to an ISP will be filtered as mentioned above. So, if you have any third party personals sending mail on your behalf, it should be specified in the records for proper flow. We can also add normal security measures like IP block list, reputation, rate limits etc. to improve the efficiency.
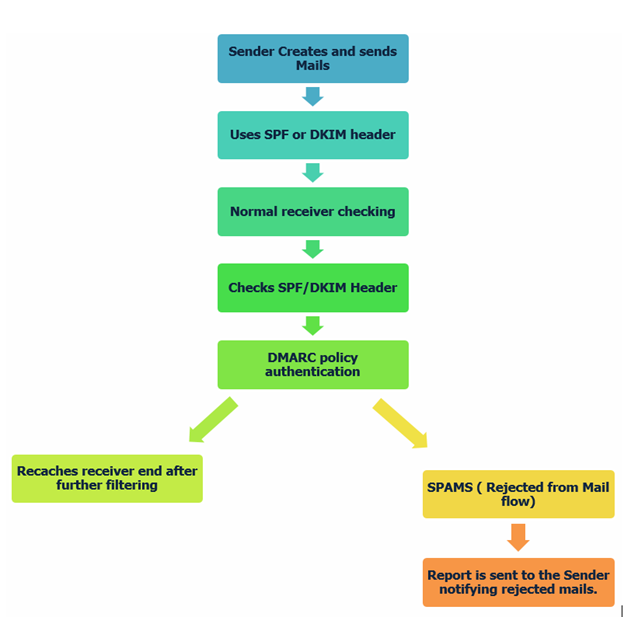
Figure 3: DMARC Working Flowchart
DMARC - Advantages
Once DMARC is set up, it really helps us to reduce spam mail from various unauthorized servers. A forged mail sent from an unreliable source, can be used to carry out an attack which could compromise the entire network or system. Since DMARC also uses SPF/DKIM inside the structure, it gives much more efficiency than other methods. It's definitely better than using weak SPF or DKIM alone is the system. Even if one of the function fails the other one backs up by providing a support to the system and helps to determine whether the mails are legitimate or not. DMARC is advised to implement on every domain to prevent attacks through e-mails and in also filtering spam mails.
DMARC - Flaws
We may think that, using SPF and DMARC would complete the holes in the mail filtering system. There is a small side effect for this method, i.e. the mail reaches the receiver end if either one of SPF or DKIM passes it in. If an attacker manages to find a way to pass SPF or DKIM, it will reach the inbox. An attacker can bypass the DMARC by creating a perfect mail copy if the following steps are followed:
- If the attacker uses a server IP that passes through SPF policy. This could be done by selecting the same email provider as the sender.
- Attacker can make use of any authorized server to create a mail; this mail will be given proper DKIM keys as other legitimate mail and would reach the receiver end.
- Let's say that the senders side is fully configured with SPF, DKIM, DMARC and the receiver side is left without any proper configuration, the mail could easily reach the receivers end, since there are no properly established filters.
The Fix
There are a lot of standards and technologies available to avoid email fraud and spams, but none of them can be said as complete solution to this problem. At some point, each and every system tend to fail. We can see SPF and DKIM implemented in wide range, but DMARC is not well supported and are not published for majority of domains. To fix the flaws that appear in this system, there are a few other techniques that could be used to increase the efficiency in stopping email frauds and spams. The following are a few such techniques:
-
Mail Inspection: There are a few simple inspection methods that help us to identify fraud mail to an extent. Some of them are mentioned below:
- Look for "From" address: From address has the senders email ID and might also contain other bit of identifying information about the sender. When normally opening the mails, most of the mail programs will hide the mail address from the "From" field. The reason to look for mail address is that, the name shown in the "From" field will be a name that you are familiar with. But the address can be of a different person. There may be a lot of users with same name, but the email ID is unique. This is a simple thing, but usually no one notices such things unless the person wants to make a reply to the received mail.
- JavaScript Functions: Email messages might contain JavaScript that can be very harmful by just opening a received mail. It's very much important to know about the JavaScript content of the one we use.
- Click carefully: Do not click every link that you see. A phishing mail might contain images or links that might activate a malicious JavaScript or might open a fake page to trap us. When a JavaScript is active, you might not be able to understand what function is currently running. To overcome this problem, one should examine the source carefully. A spam filter will detect the URL present in the mail and scan those URLs before opening.
- Check for irregularities: Check the content for any abnormalities in the message. If you have an idea of how the mail should be, compare it with the received mail to confirm the authenticity. If you have any doubt, its advised to contact the company for confirmation.
- Digital Signatures: By using features like PGP or S/MIME in a sender's email will help us to sign the mail digitally and encrypts the body of the message with a specific key. The receiver can now verify the signature with the help of the same key and confirm that the body was not edited in between. This feature is much more efficient than using DKIM signatures.
- A Secure Portal Access: If we use a web portal with login feature to send and receive mail at both end, the chance to interfere in between will be minimum. Strict encryption should be implemented at database side to avoid attacks from that side.
In short, to make the mail flow free from spoofing and fraud there is no easy one step process. DMARC is just one step towards a total spam free mail flow. Along with DMARC, the above mentioned points and features can also be included to make sure to avoid such problems.
Conclusion
DMARC plays an important role in identifying fraud mail and spams. The importance of such systems is increasing day by day, as attackers always find a way to bypass the system. As we discussed earlier, by just implementing DMARC we cannot put an end to such frauds. It requires a set of steps and functions to control the overflowing mails. This forged mail could compromise the entire network of a company. So, it's our responsibility to control such illegal activities. The organization or company might have well configured firewall or router, but one such mail can easily give access to the hacker into the system.
Reference
- http://pages2.marketo.com/rs/marketob2/images/SPF-and-DKIM-for-Email-Deliverability.pdf
- https://dmarc.org/overview/
- https://tools.ietf.org/html/rfc7489
- http://www.returnpath.com/solutions/email-security-fraud-protection/dmarc/
- https://wordtothewise.com/2014/04/brief-dmarc-primer/
- https://dmarcian.com/dmarc-inspector/
- http://kb.mailchimp.com/delivery/deliverability-research/about-dmarc




