DDoS on UPNP Devices
Denial of service (DOS) attack is an attempt to make a machine or a network resource unavailable to its users. It basically consists of methods to temporarily or indefinitely interrupt or suspend services of a host connected to the Internet, and these attacks are sent by one person or a system.
One common method of attack involves saturating the target machine with external requests in a massive amount so that it cannot respond to the valid traffic, or it responds so slowly as to make the user believe it's essentially unavailable. These attacks generally lead to a server overload. Basically, DOS attacks are implemented by either forcing the targeted system(s) to reset, or by consuming its resources so that it can no longer provide its intended service or by obstructing the communication media between the intended user and the victim so that they can no longer communicate properly. Also, DOS attacks can lead to issues in the network 'branches' around the actual computer that is being attacked.

What should you learn next?
Considering an example, the bandwidth of a router between the Internet and a LAN may be consumed by the particular attack; compromising not only the particular computer but also the entire network or other computers on the particular LAN. If the attack is conducted on a large scale, entire regions of Internet connectivity can be compromised without the attacker's knowledge or intent by incorrectly configured or flimsy network infrastructure equipment.
Symptoms Of DOS Attack:
- Unusually slow network performance (slow while opening files or accessing Websites).
- Unavailability of any particular Website.
- Inability to access any Website.
- A large hike in the number of spam emails received.
- Unintended disconnection of a wireless or wired Internet connection.
-
Long time denial of access to the Web or any Internet services.
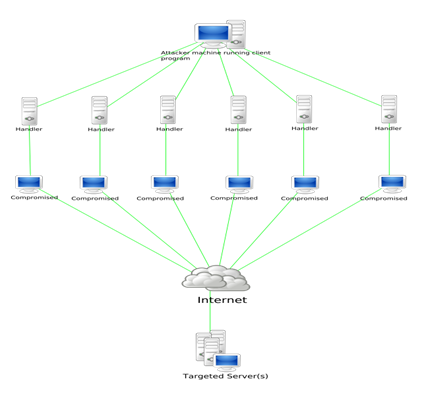
Figure 1: Representation of DOS attack
REFLECTION DDOS ATTACK
A distributed denial-of-service (DDOS) attack also involves sending forged requests of some type to a very large number of computers that will reply to these requests. Using Internet Protocol address spoofing, the source address of the target is set, which means all the replies will go to (and flood) the target. This type of attack is called the 'REFLECTION DDOS ATTACK'.
ICMP Echo Request attacks, also called the 'SMURF' attack, can be considered as one form of reflected attack. It works on the principle that as the flooding host(s) sends an Echo Request to the broadcast address of the mis-configured networks, thereby pranking hosts to send Echo Reply packets to the victim. Many systems can be exploited to act as reflectors.
DDOS attacks are an older type of attack, but reflection DDOS attacks have recently received a lot of attention right from the March when the anti-spammers Spamhaus attack took place, which was the largest DDOS attack that has taken place to date (at 300Gbps) using the reflection method. As mentioned, it's a common attack vector, but it's extremely effective when launched by an attacker with significant resources.
In a reflection DDOS attack, the attacker imitates ("spoofs") the victim's IP address and sends a request for information via UDP to servers ("reflectors") known to respond to that type of request. The servers answer the request and send or reflect the response to the victim's IP address. And hence from the servers' perspective, the victim has sent the original request.
All the data from those servers adds up to significant bandwidth, which is enough to congest the target's Internet connectivity. With the bandwidth maxed out, "normal" traffic cannot be serviced, and legitimate clients cannot get connected. Any server open to the Internet and running UDP-based services can potentially be used as a reflector.
Spoofing is the major technique that's used in a reflection DDOS attack. It is a method of tricking the reflectors by the attackers into flooding the target. Spoofing is possible because the attackers use the UDP protocol, which is a unidirectional and stateless protocol, as the transport protocol for the requests for the attack.
The victim does not require any trace back in order to locate those reflectors. They are actually identified as the source addresses (address of the reflectors) in the flooding packets received by the victim. The operator of the reflectors cannot easily locate the slave that is pumping the reflector, because the traffic that is sent to the reflector does not have the slave's source address, but instead it has the source address of the victim.
In principle, the operator can use trace back techniques such as those discussed above in order to locate the slaves in the network that is flooded. However, note that the individual reflectors send at a much lower rate than the slaves would if they were flooding the network directly. Each slave can scatter its reflector triggers across all or a large subset of the reflectors, with a combinational output being Nr reflectors, Ns slaves, and a flooding rate F coming out of each slave; then each of the reflectors generates a flooding rate of:
So a local mechanism that attempts to automatically detect that a site has a flooding source within it could fail if the mechanism is based on traffic volume. In addition, traceback techniques based on observing large volumes of traffic (ITRACE, probabilistic packet marking; but not SPIE) will fail to locate any particular slave sending to a given reflector. If there are Nr reflectors, then it will take Nr times longer to observe the same amount of traffic at the reflector from a particular slave as it would be if the slave had sent it to the victim directly. And so using reflectors provides significant protection against these forms of traceback, even if there aren't more reflectors than slaves. Against a low-volume traceback mechanism like SPIE, reflectors do not yield such an advantage; the attacker should instead assign each slave to a small set of reflectors. Thus, the use of traceback by the operator of a single reflector does not reveal the location of multiple slaves.
They can also attenuate the volume of traffic sent to them to a certain level and still serve their purpose well and effectively. This latitude on not requiring amplification consequently allows a large number of different network mechanisms to be the reflectors facilitating the attacker's task of finding a sufficient number of reflectors to launch the attack.
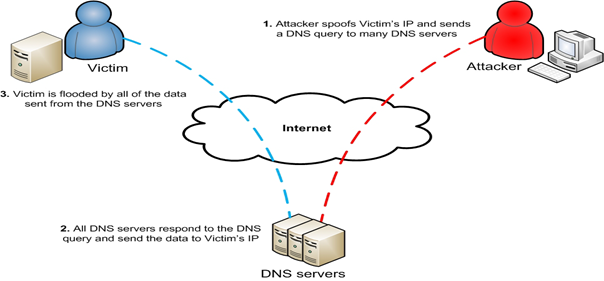
Figure 2: Representation of Reflection DDOS attack
- Common Reflector Servers Used in DDOS Attacks
- Types of servers that are commonly used in reflection attacks:
- DNS server - for scanning the Internet for open recursive servers to use as reflectors.
- SNMP servers - are also good for reflection because hosts and network devices frequently leave SNMP read access open to the Internet. And one single request can result in huge amounts of response data.
- Video game servers - many older gaming servers respond to any IP that sends certain UDP server-status queries. Then a larger response that contains volumes of information about players and their statistics are received.
- Attackers use a query type of "ANY" to return most of the data, and they often target zones containing a lot of DNSSEC data, which gives a magnified response.
-
Steps to Mitigate DDOS Attack
UPNP Devices
UPnP is a protocol designed to automatically configure networking equipment without user intervention. UPnP allows Xboxes (video game brand) to tell your firewall to punch a hole through so you can play games. UPnP also allows malware to punch holes in your firewall, making access easier for attackers.
A universal plug and play device is ready when it is plugged in. It gets ready to be used once its software is loaded. UPnP has the major quality to learn and communicate with other devices and use their capabilities. UPnP is independent from any programming language and platform. That's why it is widely usable. Since previously UPnP devices had to know their protocols to communicate, it was impossible to communicate with all the devices. In 1999 UPnP forum developed UPnP, and from then onwards, most devices support UPnP and can communicate over UPnP Protocol.
Six steps defining the working of UPNP protocol are:
It isn't a good idea to implement something that can disable security features without authentication or the knowledge of the person controlling the device. So the risk of rogue devices/software on the inside that exploits UPnP is more, and hence the danger of UPnP accepting information from outside is even worse. Many routers do not provide an option to disable UPnP, and some others have an option, but it doesn't help.
Vulnerability in UPNP devices
Vulnerability in the Universal Plug and Play (UPnP) Internet protocol exposes millions of Internet devices to Distributed Denial of services (DDOs) attacks.
Attackers use reflection and amplification DDOS attacks to exploit the Simple Service discovery Protocol (SSD), which is a standard Internet protocol that facilities communication and coordination between many UPnP devices including routers, webcams, Smart TV's and printers. This protocol is a section of the Universal Plug and Play (UPnP) Protocol standard. SSDP comes enabled on millions of devices in homes and offices. Attackers have been using these protocols to launch DDOS attacks that amplify and reflect network traffic to their targets.
Malicious actors are using this new attack vector to perform large-scale DDOS attacks. The count of UPnP devices that would behave as open reflectors is a large number, and many of them are home-based Internet-enabled devices that are difficult to be patched. Action from firmware, application and hardware vendors must occur in order to mitigate and manage this threat.
Geographically, Korea has the highest number of vulnerable UPnP devices distribution, followed closely by the countries US, Canada, Argentina and Japan. Researchers explain that the huge number of vulnerable devices, which is approximately 38% of the 11 million UPnP devices, will be a challenge to perform mitigation, patch management, updates and cleanups. The massive number of vulnerable devices also gives hackers more chances for attacks.
The massive amount of vulnerable UPnP devices may give a chance to the development of a new tool that can take advantage of the SSDP and SOAP protocol, which could lead to the development of UPnP device based reflection attack tools and botnets being constructed in DDOS attacks.
DDOS attacks on UPNP devices
A malicious hackers starts by identifying vulnerable UPnP enabled devices on the network. This is achieved by sending a SOAP (Simple Object Access Principle) request, which is called M-SEARCH, to UPnP devices. The M-SEARCH then identifies the vulnerable devices and then the devices respond to the SOAP requests with the HTTP location of its device XML description file.
The hacker then sends malicious requests to the identified vulnerable devices after spoofing the address of the targets and causing a reflected and amplified response. Then the volume of traffic that's created depends on many factors, which include the size of the device description file, the operating system and also the UUID (Universally Unique Identifier).
The Simple Object Access Protocol (SOAP) is used to deliver control messages to UPnP devices and pass information back from the device identified to be vulnerable. Attackers have discovered that SOAP requests can be crafted so as to elicit a response that does the function of reflecting and amplifying the packet, which then could be redirected towards a target. By employing a great number of devices in the activity, attackers create large quantities of attack traffic that can be aimed at selected targets.
The two techniques used to scan and find the vulnerability of the UPnP devices are: ssdpscanner.py for scanning and ssdpattack.py to detect if the system is already attacked.
Steps to mitigate the vulnerability on UPNP devices
Unfortunately there are no sure ways to mitigate DDOS attacks on UPnP devices due to the large number of vulnerable UPnP devices and due to their very wide geographical distribution.
However, Akamai security experts recommend two ways:
2.1) blocking all wide-area Network (WAN) – based UPnP requests to client devices,
2.2) disabling UPnP service on devices where it is not a basic requirement and proactively patching and updating UPnP devices that are open to the Internet.
Conclusion
The rise in reflection and amplification of DDOS that involves UPnP devices has become a serious threat to the Internet infrastructure. It is clearly evident that DDOS attack can be an attack that happens once the system is well identified, developed and incorporated with new resources. The coming future of Internet users could be not very smooth and efficient if these types of attacks continue to develop and refine their techniques and tools. There should be more action from the firmware, application and hardware vendors to mitigate and manage these types of threats.
References
http://www.ddosattacks.biz/attacks/reflection-ddos-attacks-how-they-work-and-what-you-can-do/
http://www.icir.org/vern/papers/reflectors.CCR.01/node1.html
https://cert.litnet.lt/en/docs/ntp-distributed-reflection-dos-attacks
http://security.stackexchange.com/questions/35571/how-does-a-reflection-attack-work
http://www.erdincaydin.net/Text/BigBang.html

FREE role-guided training plans
http://securitygladiators.com/2014/10/17/upnp-devices-risk-ddos-attacks/




