Cracking the Maze of Advanced Persistent Threats!
Advanced Persistent Threats, as the name suggests, are advanced, persistent and deadly in their nature. The ghost of APTs can affect any organization at any moment of time. Security specialists have to face the ordeal of cracking the never-ending maze of APTs.
Security professionals need to employ a wide range of techniques and tools in their arsenal, both automated and manual in nature, including threat modelling, attack vectors, and the most difficult of all tasks: identifying the attacker. Various components include monitoring of logs, analysing the anomalous behaviours within the network traffic and keeping the staff well aware and trained to face any emergency.
Learn Digital Forensics
APTs are hard to identify and usually come as a zero-day attack. Identifying that you are under an attack itself is hard to do, but once you've identified it, you start the real work of combating it and safeguarding your assets. The red signs of APT attacks are network exploration (also called pivoting) and data exfiltration.
Of late, APTs have challenged the best of security brains in combating them. This article identifies the processes and tools which can be used by Emergency Response Teams of organizations to strengthen their defence against APTs.
Network Traffic analysis and Monitoring Logs
By now, you must be aware that the native nature of APTs is data exfiltration from the target network to Command and Control servers. Without this, the whole purpose of APTs is a failure attempt. Thus, network traffic analysis and monitoring of logs are quintessential parts of defence against APTs. Let's examine the following screenshot:
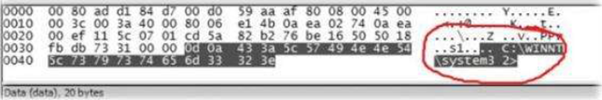
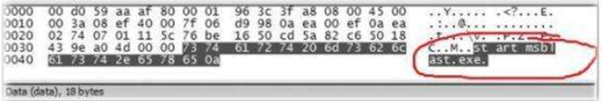
In the above screenshot, we see that some network capture is trying to navigate C:WindowsSystem32 and a further capture shows that a malware is finding its entry into the network. This is one such example which exemplifies the importance of network analysis and monitoring logs. A few activities like screenshot captures and a sudden increase in outgoing traffic over various intervals are unexpected and suspicious in nature. When these are happening without any permission, it should ring bells for the Emergency Response Teams.
Logs on the other hand, if comprehensive, help to identify any connections made to unidentified systems/networks. For example, if the machine within your datacentre is trying to connect to an unknown server, then it could be a potentially malicious connection if not identified and categorised correctly.
A survey by Verizon revealed that 75% of APT attacks only take minutes to make an initial compromise of the target. The ultimate purpose of APT – data exfiltration - took minutes to get accomplished in 38% of the cases, whereas the detection rate spanned over months in 54% of the cases, and the restoration from the threat took anywhere between days to weeks in 32% and 38% of the cases, respectively.
Traffic analysis tools like NetFlow can be used in bandwidth monitoring or querying servers which make connections to the same IP address or port. This can help in finding the source where an attack might have originated. To make results more productive, the ERT should define expected behaviours and thus make it a baseline. This will help during attacks done using Zero-days because in those cases the behaviour of the network falls outside the defined baseline, indicating a possible intrusion. The categorization of network segments to high-risk and low-risk segments will help relax certain baselines when resource availability is tight on the management side. The rules must be carefully evaluated and reviewed by the technical board and all the stakeholders. Thus, any intricacies can be avoided.
A tool like OSSEC, which is an open-source Intrusion Detection System, can provide analysis of logs, file checks, and Windows registry monitoring. This can also be used to integrate with 3rd party firewalls, IDS, web servers, switches and routers. A zero day exploit is always undetectable for an administrator, but he can always try to detect the payload being used along with it.
IDS systems can play a very important role in detecting APT activity. For example, a remote access tool like Poison Ivy operates on port 3460. As an administrator, the policies can always be set to check for outgoing traffic via this port, and also to compare signatures of the initial communications between the RAT and the C&C Servers. Unlike other attacks and defences, APTs require a fine mixture of manual as well as automated efforts.
The inherent nature of APTs is to run as a service. The reason behind this nature is to gain elevated access levels and the ability to read the memory status of other processes running on the system. Organizations run DMZ's a.k.a Demilitarized Zones. If it is not supposed to have traffic on ports other than HTTP/HTTPS, DNS etc., then alerts must be configured to check for any traffic other than these specified services. This is done by configuring the Access Control Lists.
A few other criteria to check are the ratio of upload versus download data. An unusually high upload data can hint at data exfiltration, whereas unusually long SQL queries hint that your organization might be under an attack already. I have provided the screenshot of Wireshark in the initial section of this article. It's a very beneficial tool in network traffic analysis. Attackers can also use fast-flux methods to hide their original network, by using an ever changing network of compromised zombie systems. Identification of such IPs is a big step towards identifying the source of the APT.
Data exfiltration is the main aim of an APT attack. Use a tool like Squid to permit or deny traffic to prevent an ATP from sending data out of the network. Security teams must be updated about the latest trends in attack vectors and threat landscape. SquidGuard can be used to blacklist known IP addresses and domains. Another tool which an administrator can consider is called Security Onion. Security Onion can be seamlessly integrated with Squid. Using a chain of IDS's like Snort, NetworkMiner, Snorby, etc., APTs can be detected early with real-time reporting and visualization. APTs are targeted in nature but it doesn't mean no malware would be used to initiate an attack. Attack initiators can be as simple as phishing – for example, the RSA SecureID case.
Behavioural Analysis of an APT
As said in the above paragraph, any malware can be used to initiate an attack, and reversing the malware to understand its behaviour is key to going one step closer to the source of an APT. The behavioural analysis obviously cannot be done on a live network under attack. The sample must be contained in a virtual lab to isolate its behaviour and understand its root.
Tools like Process Explorer, Process Monitor, VMMap, Regshot, etc., can be used to aid in the behavioural analysis phase. These tools compare registries with stable and affected snapshots, provide information about DLLs currently used and loaded in the memory, identify the sources of memory usage, and so on. These details even through micro in nature, can add up in the macro analysis to provide useful inputs. The advanced nature of APTs makes sure that the attacker clearly knows many details inside the organization. These can be obtained via methods described in the "Advanced Persistent Threats – Attack and Defense" article published on June 13, 2013. Malware of these specific application types look for information in the memory and storage. The most usual step includes checking the registry values to see which antivirus is installed and then take actions accordingly.
Malware have evolved from simple naughty pranks to advanced polymorphic dynamic bots which can affect millions of boxes in seconds. Obfuscated malwares can be detected using certain tools like IDA or Ollydbg to disassemble the code first. Remnux is a forensic Linux distro which can be used in such scenarios. It can be used as a pivot when the malware executes the "Connect to Command and Control Server" routine. As usual, this might include the HTTP protocol to establish connection channel.
We have seen time and again that APTs require special skills and out of the box investigative skills to trace and defend one self. A real time example of DuQu, which was uncovered as a part of Stuxnet investigation, was unable to be deciphered by a single group of researchers. The research was crowd sourced and found that most of the code, which was in C++, had a segment which looked like alien language to the experts. It seemed to be an Object Based C program, which indicated that DuQu was made by old school programmers, using well tested code of an existing malware.
Learn Digital Forensics
Combating APTs without the help of a security community is a waste of effort. Organizations must tie up with the hacker community and get to understand their defence systems to try to safeguard against the bad guys. Well, only a bad guy can think like a bad guy. We can surely combat APTs with greater effectiveness working as a team.





