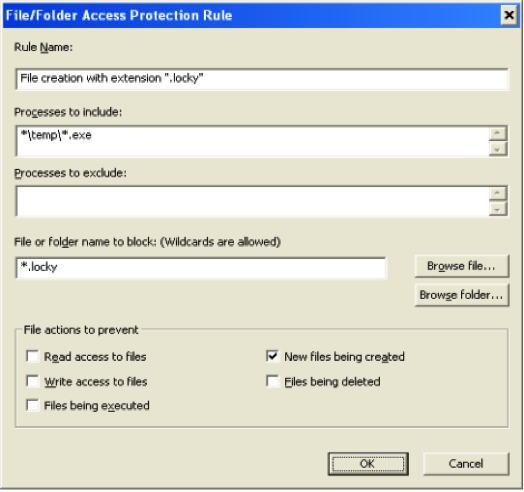
Case Study of Phishing for Data Theft/Ransom: Locky Ransomware
Phishing & Ransomware - Locky Ransomware Case Study
Related Phishing Articles:
[clist id="1470243405619" post="35256"]
Prologue to Ransomware
Ransomware is a malicious application that is built to lock files and prevent or limit users from accessing their computer system until a ransom payment is made.
See Infosec IQ in action
Today's ransomware is a complex, sophisticated threat, damaging clients in numerous areas around the world, especially people from developed and tech-focused economies.
Cybercriminals use multiple strategies to spread ransomware. The most common methods include spam emails, advertisement media, and exploit kits.
- In phishing emails, an attacker infects multiple users at the same time and demands the ransom.
- Using an exploit kit, the attacker uses zero-day exploits to penetrate computer systems.
History of Ransomware
Previously, cybercriminals were using ransomware as a weapon for extortion by infecting multiple victims. Researchers say ransomware has already made millions through extortion.
Recently, cybercriminals were successful in infecting the Hollywood Presbyterian Medical Center’s computer systems with ransomware. Because of the way Locky is spread (via malicious Word documents), it’s likely that a Hollywood Presbyterian employee fell for a phishing scheme and opened a document that looked like a hospital invoice. It’s unsure who opened the file, but when the problem was reported on February 5, 2016, it had already spread rapidly.
The ransomware attack was network-aware and replicated itself through network shares and mapped drives and was eventually successful in taking down the entire hospital network. According to the initial report, the network was down for more than a week. Hospital staff was reduced to using fax machines and notepads in order to continue operations. Many patients were transferred to other facilities with working networks.
The ransomware demanded a payment of 40 Bitcoins, equal to about $17,000. The simplest (though not always best) method suggested by researchers is to pay the ransom and obtain the decryption key to recover the data.
In this case study, we will learn about the actual strategy of cybercriminals, how they spread malware, and take a deep look at malware IOCs and preventive measures. We will start with a study of Locky Ransomware.
Summary:
How Do Cybercriminals Spread Ransomware?
We will start with the most commonly used methods for spreading ransomware.
Cybercriminals start with a basic email to a single representative or a group of staff members, using a basic headline used commonly in our day-to-day work, such as “Image Scan,” “Invitation to connect on LinkedIn,” “Mail delivery failed: returning message to sender,” “Dear <insert bank name here> Customer,” “Undelivered Mail Returned to Sender,” and so forth. (Refer to image 1.2 for reference.)
In the body of the email, the cybercriminals construct a straightforward Microsoft Office document with unsafe macros, which then downloads malicious code from an archive once it is executed. The cybercriminal utilizes an encrypting system to avoid detection from security products like Iron Port (SPAM Filter and Anti-virus), etc.
Cybercriminals behind ransomware do not care who they target as their victims. Their ultimate aim is only to get the ransom. They target homes, businesses, and public agencies alike. As mentioned, the unfortunate Hollywood Presbyterian Hospital employee likely opened something that looked like an invoice or an important policy change from the CEO or HR department.
Contextual Analysis of Locky Ransomware:
According to a study, cybercriminals have started phishing assaults with ransomware, targeting multiple industries, including healthcare, gamers, and businesses. No longer merely the realm of the PC, cybercriminals have also built MAC OS ransomware, and can even target mobile devices. Truly, no one is exempt.
[cta id="1470247812898" post="35896"]
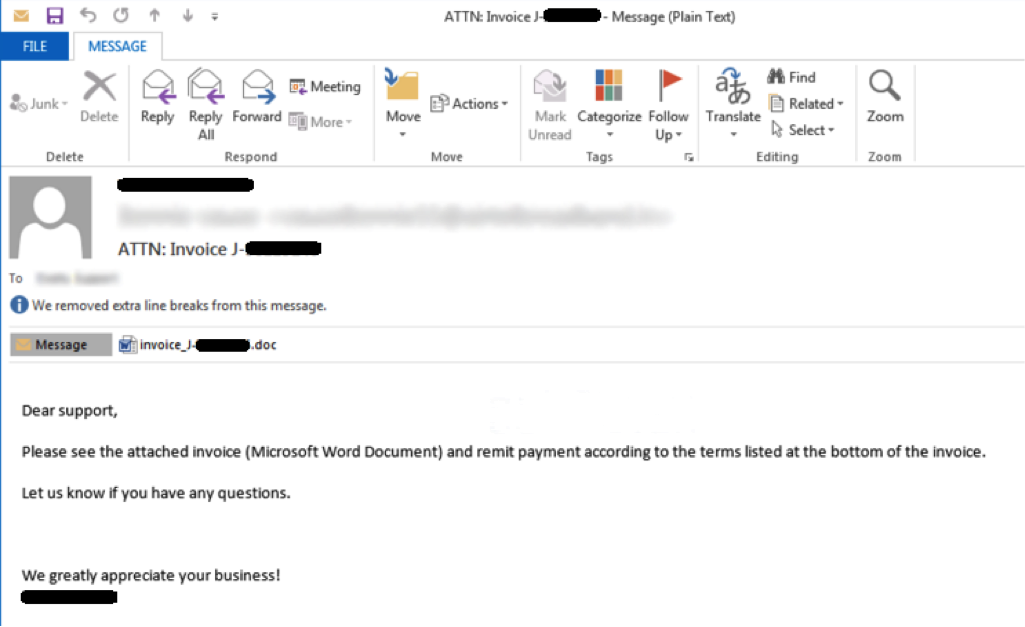
Often, cybercriminals use a subject like “Attn: Invoice J-xxxxxxxx” to spread malware. This is because it is the format of a common email subject line, and is left deliberately vague because it ensures that the user will open the document to get the rest of the details. An example of one of these emails can be seen below:
1.2 Sample email used to distribute malicious applications like ransomware
In this situation, the attached malicious *.doc file is attached to an email with the same title. Once the document is opened, the text shows encrypted data. It will ask you to click on "Enable Editing" to make the text format readable. Once the user enables these macros, they will download an executable from malicious binary-hosted servers and execute it. The file then copies itself to a %temp% folder, executes itself, and starts to encrypt the files on the victim’s computer. Locky then scans all the local drives and network shares for encryption. It may use an AES encryption algorithm.
Characteristics and Symptoms:
Locky is a type of malware that encodes the compromised user’s files available in the system in order to collect a payoff. The records are encoded utilizing an RSA-2048 and AES-1024 calculation. After effectively self-executing, Ransomware-Locky duplicates itself into the %temp% envelope with an arbitrarily name and ".exe" extension.
e.g.: C:Users<UserProfile>AppDataLocalTemp<random name>.exe
The malware then adds itself to the "Run" registry section with a quality name "Locky," with information indicating that the dropped record is in the %temp% index. The fundamental pernicious document will be erased after it duplicates itself to the %temp% directory and executes the replicated record. The new process begun from the %temp% directory creates an extraordinary ID (Personal Identification ID) utilizing the following system:
- Get volume GUID (windows drive) path.
Ex: \?Volume{a7c7a6b1-2d27-11e0-aaa3-806d6172696f}
- Calculate MD5 of the GUID
Only GUID with braces considered for MD5 calculation
“{a7c7a6b1-2d27-11e0-aaa3-806d6172696f}”
MD5 of above GUID string: 50DA5BC8E75B1354C350BCACA54E3AFC
- First 16 characters considered as Personal Identification ID
Personal Identification ID: 50DA5BC8E75B1354
Ransomware-Locky additionally removes the volume shadow copies from the victim’s systems, consequently preventing the client from restoring the encoded files. Shadow duplicate is a Windows highlight that helps clients make reinforcement duplicates—previews—of PC records or volumes. Ransomware-Locky utilizes the accompanying summon to erase all the shadow volume duplicates on the PC:
"Vssadmin.exe Delete Shadows/All/Quiet"
Ransomware-Locky contacts the CnC server to get the Public Key and also the recuperation direction content and stores.
The public key and recovery instruction text in the registry:
- POST request to get public key:
id=50DA5BC8E75B1354&act=getkey&affid=1&lang=en&corp=0&serv=0&os=Windows+XP&sp=3&x64=0
- POST request to get recovery instructions:
id=50DA5BC8E75B1354&act=gettext&lang=en
NOTE: Malware encrypts the above POST ask for before posting request. Ransomware-Locky scrambles the documents with the following extensions:
.asm, .c, .cpp, .h, .png, txt, .cs, .gif, .jpg, .rtf, .xml, .zip, .asc, .pdf, .rar, .bat, .mpeg, .qcow2, .vmdk .tar.bz2, .djvu, .jpeg, .tiff, .class, .java, .SQLITEDB, .SQLITE3, .lay6, .ms11, .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .potx, .potm, .pptx, .pptm, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .dotm, .dotx, .docm, .docx, wallet.dat and etc.
Ransomware-Locky ignores the path and filename with the following strings from encryption:
Application Data, AppData, Program Files (x86), Program Files, temp, tmp, Thumbs.db, $Recycle.Bin, System Volume Information, Boot, Windows.
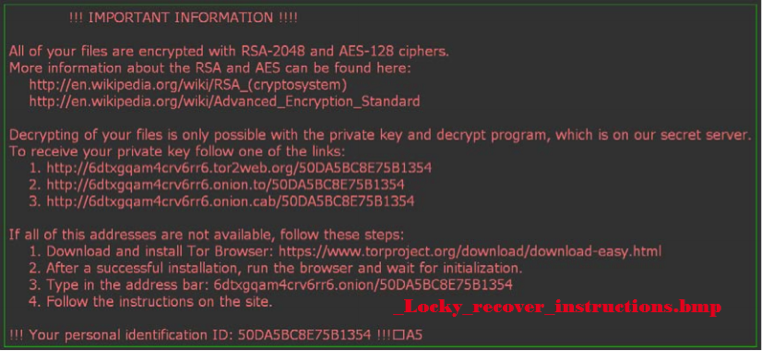
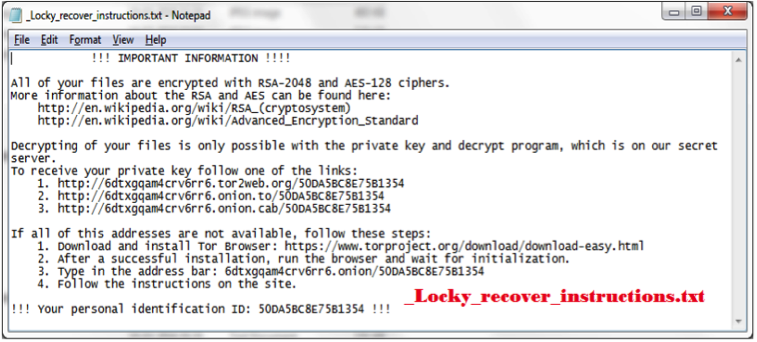
After files are successfully encrypted, malware opens the recovery instructions image and text file. Malware likewise changes the desktop background with the recuperation direction picture record:
- _Locky_recover_instructions.bmp
- _Locky_recover_instructions.txt
_Locky_recover_instructions.bmp
_Locky_recover_instructions.txt
Pointers of Compromise, i.e., IOC
The accompanying pointers can be utilized to recognize potentially contaminated machines in an automated way. We expect the client's machine to be infected if:
- The following registry key has been added to the system:
- HKEY_CURRENT_USERSoftwareLocky
"id" = < Personal Identification ID>
“pubkey” = <RSA public key received from the CnC Server>
“paytext” = <Content of “Locky_recover_instructions.txt”>
“completed” = “0x1” [This value will be added after completion of encryption]
The following registry entry would enable the Trojan to execute every time Windows starts:
• HKEY_CURRENT_USER SoftwareMicrosoftWindowsCurrentVersionRun
After the malware successfully completes encrypting the comprised system, it deletes itself from the %temp% directory and also removes the “Run” registry entry.
2. There is network traffic to the IP addresses mentioned below:
- 95.181.171.58
- 185.14.30.97
- 195.22.28.196
- 195.22.28.198
- pvwinlrmwvccuo.eu
- cgavqeodnop.it
- kqlxtqptsmys.in
- wblejsfob.pw
Preventive Measures
It is recommended that you follow preventive measures to stay away from ransomware infection, e.g., documents (files), registry, and the URL can be accomplished at different layers.
The end user may take extra efforts to follow these measures to avoid Ransomware infection:
- Perform a daily or hourly backup of important data files and folders. Utilize numerous online resources that are accessible, such as Google Drive, Dropbox, Jio Drive, and so forth for backup.
What to do if you are the victim
Report your issue to an IT team, information security team, or forensics team immediately. They will be best qualified for any suspicious or surprising activity. The ultimate goal of this article is to make users aware of security safeguards so they will not be the victims of these kinds of assaults.
To enhance your technical savvy and increase your network safety, consult the SecurityIQ website. It is a free software service incorporating tools that can be used to create fake phishing templates and conduct fake phishing campaigns on your friends, family, co-workers, or employees. They can also provide reports on who fell for the phishing campaign and who did not, as well as interactive information modules that your friends, family, or employees can watch to practice their newfound security skills.
Ransomware destroys online lives and robs users of untold fortunes. The best defense against ransomware is the human element. Stop ransomware before it can start by becoming more savvy about phishing and cybersecurity. Please visit https://securityiq.infosecinstitute.com/?utm_source=resources&utm_medium=infosec%20network&utm_campaign=infosec%20iq%20pricing&utm_content=hyperlink and sign up for your free account today.
References:
http://howtoremove.guide/locky-virus-ransomware-file-removal/
See Infosec IQ in action