Car Hacking: You Cannot Have Safety without Security
Introduction
The theme of the car hacking is increasingly discussed by the media and within the security community. At one time, the exploits of hackers that have hijacked a car were the subject of movie scenes. Today they are a disturbing reality that we discuss in this article.
One of the effects of the massive introduction of technology in our vehicles is car hacking. The term refers to the possibility that a hacker can compromise some of the technological components within our cars.
Learn ICS/SCADA Security
Modern cars contain upwards of 50 electronic control units (ECUs) that exchange data within an internal network. The safety of the automobiles relies on near real time communication between the different ECUs for predicting crashes, performing anti-lock braking, and much more.
Recently, Charlie Miller, one of the most popular hackers, demonstrated working with Chris Valasek, director of security intelligence at IOActive, the possibility to hack a car by breaking into the control system of the vehicles.
Cars are complex systems composed of numerous intelligence components that control different functions of the vehicle. The massive introduction of electronics requests a serious approach to the overall security of those parts.
"Automotive computers, or Electronic Control Units (ECU), were originally introduced to help with fuel efficiency and emissions problems of the 1970s but evolved into integral parts of in-car entertainment, safety controls, and enhanced automotive functionality.
This presentation will examine some controls in two modern automobiles from a security researcher's point of view. We will first cover the requisite tools and software needed to analyze a Controller Area Network (CAN) bus. Secondly, we will demo software to show how data can be read and written to the CAN bus.
"Then we will show how certain proprietary messages can be replayed by a device hooked up to an ODB-II connection to perform critical car functionality, such as braking and steering.Finally, we'll discuss aspects of reading and modifying the firmware of ECUs installed in today's modern automobile," reports an abstract related to the presentation done at the Black Hat security conference in August 2013.
The intent of numerous specialists is to approach the car with the eyes of a hacker to explore security issues and demonstrate how it is possible to exploit numerous flaws to interact directly with principal components of a vehicle, including braking and steering.
Figure 1 - Steering Video POC by Charlie Miller
Electronic Control Units (ECUs) and Controlled Area Network (CAN)
Electronic Control Units communicate together on one or more bus, based on the Controlled Area Network standard.
The CAN bus (controller area network) is the standard in the automotive industry, designed to allow data exchange between ECU and devices within a vehicle without a host computer. The CAN bus is also used in other industries, including aerospace and industrial automation.
In the automotive, ECUs exchange CAN packets, and every packet is broadcasted to all the elements on the same bus, this means each node can interpret it. The principal problem is that packets lack a sender ID and the protocol doesn't implement an efficient authentication mechanism. This means that attackers can capture every packet, spoof the sender ID, and authenticate itself to the ECU, which does not correctly check the identity of the sender ID.
The CAN protocol implements two different message frame formats: base frame format and the extended frame format. The only difference between the two formats is that the first one supports a length of 11 bits for the identifier, while the extended format supports a length of 29 bits for the identifier, made up of the 11-bit identifier ("base identifier") and an 18-bit extension ("identifier extension").
CAN standard implements four types of frames:
-
Data frame: a frame containing node data for transmission
-
Remote frame: a frame requesting the transmission of a specific identifier
-
Error frame: a frame transmitted by any node detecting an error
-
Overload frame: a frame to inject a delay between data and/or remote frame
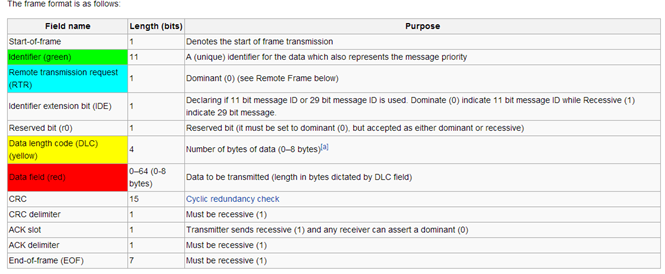
Figure 2 - CAN frame format (Wikipedia)
CAN is a simple low level protocol that doesn't implement any security features. The security must be implemented at a higher level; applications are responsible for implementation of security mechanisms.
"Password mechanisms exist for data transfer that can modify the control unit software, like software download or ignition key codes, but usually not for standard communication."
A hacker sending specifically crafted packets to target ECUs on the CAN could be able to modify their behavior or totally reprogram the units.
The State of the Art for Car Hacking
Today's vehicles are equipped with connected computers that could be exploited by an attacker for various purposes. To prevent similar offenses, US auto-safety regulators decided to start a new office focusing on these categories of cyber threats.
"These interconnected electronics systems are creating opportunities to improve vehicle safety and reliability, but are also creating new and different safety and cyber security risks," declared David Strickland, head of the National Highway Traffic Safety Administration.
Car hacking could be conducted to exploit new generation vehicles that are even more connected to the Internet, with each other and to wireless networks. We have to consider the fact that numerous companies are starting to think of cars as a node of an immense network that is able to acquire information from the environment to provide data useful for many services for the population of smart cities. Modern vehicles are equipped with sophisticated controllers that manage in real time an impressive amount of information. The controller of a luxury car has more than 100 million lines of computer code, while software and electronics account for 40% of the cost of the car. Every technological component in a vehicle and communication channel could be attacked by cyber criminals.
What are the principal methods to hack a car?
The most accredited methods of attacks are:
- Exploit of Telematics System. The vehicles are equipped with systems that allow them to communicate with a remote center to pass their position, and in the future a growing number of car manufacturers could also provide telemetry services for a remote diagnostic that could prevent accidental crash and electronic fault. Today, hackers theoretically could already exploit similar systems installed on the car, for example an anti-theft system that remotely arrests a stolen vehicle. Once access to a vehicle is obtained, the attackers could interact with every component on the car through the CAN bus and modify their parameters.
- Malware exploits – The attackers could infect some of car components, modifying their behavior. A malware could be injected in different ways, for example, using a USB stick inserted into MP3 reader or a wireless technology (WiFi or Bluetooth).
- Unauthorized Applications – Cars are equipped with on board computers that can execute or download applications. Also for cars, these applications could be provided by malicious and unauthorized third-parties. Let's think of the update of any software on-board; an attacker could provide malicious code to the car "masqueraded" as an update and to execute in this way unauthorized software with needed privileges.
- OBD – specifically written software could exploit the OBD-II (On-board diagnostics) port for their installation. Once the connector is accessed via the CAN bus, it is possible to monitor every component connected to it.
- DOOR LOCKS and KeyFobs – an attacker could emulate the presence of access code used by these two systems. In this way he could control locks and start/stop for car engines.
Proof of the Concept of Car Hacking
Now that we have understood how hackers consider our vehicles, which are the possible attack vectors and how the "smart" components in our cars dialogue to each other, let's give a look to a couple of proofs of concepts proposed by the hacking community. Our vehicles are comparable to a network of computers that communicate in "unsecure" way on the internal bus, so it could be relatively easy to hack them. As anticipated, the popular hacker Charlie Miller and the researcher Chris Valasek have demonstrated that it is possible to take control of part of a couple of vehicles they used for the demonstration.
Car hacking is not a new concept. Already in the past, a group of researchers have exploited weaknesses in the electronic control units (ECU), but Miller and Valasek published a study of car architecture that includes a series of new attacks they have developed, that allowed them to control braking, steering and other functions in some vehicles while they were driving.
The security experts were able to control the vehicle behavior by sending large numbers of controller area network packets to the system. In a few words, the packets they sent arrived before the legitimate packets to the ECUs that accepted the instructions they contained.
The paper published by the researchers demonstrated how it is possible to hack a vehicle, sending both normal packets and diagnostic packets on the CAN bus. For obvious reasons, I'm proposing one example of both types of attacks, inviting the reader to prove the study.
The researcher tested the "hacks" on a couple of vehicles, a Ford Escape and a Toyota Prius. The attacks with normal packets allowed them to manipulate the following components:
- Speedometer
- Odometer
- On Board Navigation
- Steering
- Speedometer
- Braking - Toyota
- Acceleration
Manipulation of Speedometer with a Normal Packet via CAN Bus (Ford Prius)
As explained by the two researchers, it is easy to detect the CAN packet injection to manipulate the values of RPM and speed displayed to the driver. In the Ford, the information is managed by a packet having the ID equal to 0201 on the high speed CAN network.
The packet format is:
[AA BB 00 00 CC DD 00 00]
Where AABB is the rpm displayed and CCDD is the speed. To change these values the team used the following formulas:
Speed (mph) = 0.0065 * (CC DD) - 67
RPM = .25 * (AA BB) - 24
For example, let's see what's happen by providing the following data in the CAN packet.
[23 45 00 00 34 56 00 00]
The following code would set the RPM and speedometer:
y = pointer(SFFMessage())
mydll.DbgLineToSFF("IDH: 02, IDL: 01, Len: 08, Data: 23 45 00 00
34 56 00 00", y)
That produced a speed of 0x3456 * .0065 - 67 = 20.1mph and an RPM of 0,25* 0x2345-24= 2233 rpm, considering that hexadecimal 3456 equals 13398 in decimal and 0x2345 equal to 9029.

Figure 3 - Manipulation of Speedometer made as Proof of concept
Kill Engine – Ford with Diagnostic Packet via CAN Bus (Ford Prius)
As anticipated, it is also possible to use a diagnostic packet to modify the behavior of many components in a car. The researchers demonstrated for both vehicles that is possible to conduct numerous operations, including:
- Security Access
- Brakes management
- Kill engine
- Lights flashing
- Horn On/Off
- Seat Belt Motor Engage
- Doors Lock/Unlock
- Modification Fuel Gauge
Differently from normal operations, diagnostic activities against an ECU need to be authenticated, but as we will see soon weak implementation of the authentication process exposes users to serious risks.
Let's consider the Parking Assist Module (PAM) ECU. The authentication on this component for the Ford Prius appears weak because it is implemented through a challenge/response process that is based always on the same seed sent by the unit. This means that the response is always the same and it was a joke for the attackers to sniff it, perform a SecurityAccess against PAM, or in the worst case "brute force" it.
Analyzing the authentication handshake, it is possible to note that it used always the same seed 11 22 33. This is an ideal situation for car hacking, but in other cases things could get more complicated. Anyway an attacker could even get the key for reverse engineering the firmware, which equips the targeted component.
IDH: 07, IDL: 36, Len: 08, Data: 02 27 01 00 00 00 00 00
IDH: 07, IDL: 3E, Len: 08, Data: 05 67 01 11 22 33 00 00
IDH: 07, IDL: 36, Len: 08, Data: 05 27 02 CB BF 91 00 00
One of the more interesting attacks proposed by the researcher relates to the manipulation of the engine that could be obtained regulating the level of gas / air. In this specific case, the Ford used for the test has a particular RoutineControl 4044 that kills the engine in case of anomalies.
The packet used in the attack is:
IDH: 07, IDL: E0, Len: 08, Data: 05 31 01 40 44 FF 00 00
The parameter in bold appears to be some kind of bit-field on which cylinder to kill, so by sending FF it is possible to shutdown all the cylinders.
By repeatedly sending the above packet, it is possible to kill the engine by blocking the re-start until the attacker stops sending the packet.
The disturbing thing is that this attack doesn't need the establishment of a diagnostic session, and it works at any speed.
Remote CAN Hacking Tools, Not So Expensive
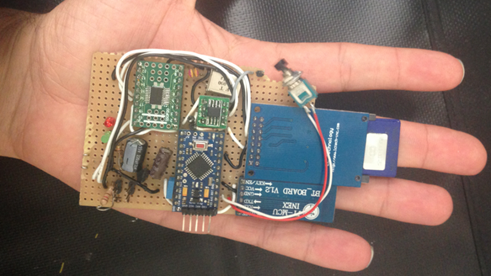
Hacking a car remotely is a scary reality. Recently security researchers Javier Vazquez-Vidal and Alberto Garcia Illera have designed a kit to control a car made up of a tiny device smaller than a smartphone. The two researchers called it CAN Hacking Tools (CHT) and they will present it at the Black Hat Asia security conference in Singapore. Now we are familiar with CAN Bus and the way various components of the car exchange data.
Figure 4 - CAN Hacking Tools (CHT)
Hacking a car has never been so easy and cheap. The Kit proposed by the researchers costs less than $20, and using it, an attacker can take complete control over a car, including steering and brakes.
We saw in the past that through the Controller Area Network (CAN) bus it is possible to access every function of the car, including control locks, steering and brakes, and also in this case the researchers decided to exploit it.
"Small gadgets they built for less than $20 that can be physically connected to a car's internal network to inject malicious commands, affecting everything from its windows and headlights to its steering and brakes," reported Forbes.
The CAN Hacking Tools was designed to inject malicious code from CAN ports and send wireless command from a PC nearby.
"It can take five minutes or less to hook it up and then walk away … We could wait one minute or one year, and then trigger it to do whatever we have programmed it to do," says Vazquez Vidal.
Javier Vazquez-Vidal and Alberto Garcia Illera have demonstrated that is possible hack a car with their CAN Hacking Tools device, testing it aganst four different vehicles and "their tricks ranged from mere mischief like switching off headlights, setting off alarms, and rolling windows up and down to accessing anti-lock brake or emergency brake systems that could potentially cause a sudden stop in traffic."
The version of CHT tested by the researchers communicates only via Bluetooth, but the experts are already upgrading it to use a GSM cellular radio that would make possible the control of the device installed on the car from miles away.
"In some cases, the attacks required gaining under-the-hood access or opening the car's trunk, while in other instances, they say they could simply crawl under the car to plant the device. For now, the tool communicates via only Bluetooth, limiting the range of any wireless attack to a few feet. But by the time the two researchers present their research in Singapore, they say they'll upgrade it to use a GSM cellular radio instead that would make it possible to control the device from miles away."
As remarked by the researcher, a car with this network today lacks any security mechanism.
"All the ingredients of their tool are off-the-shelf components, so that even if the device is discovered, it wouldn't necessarily provide clues as to who planted it. It's totally untraceable … A car is a mini network, … And right now there's no security implemented."
Hacking Detection
Standing to the analysis conducted by Miller and Valasek, the detection of attack is quite easy to do. They referred the possibility to simply implement an anomaly detection mechanism.
Defining a series of patterns for "normal" behavior of any component in a vehicle, it is possible to detect any suspicious activities and activate countermeasures. A possible implementation could be based on the analysis of the different CAN packets over the time, as Miller and Valasek proposed in the below graphic.
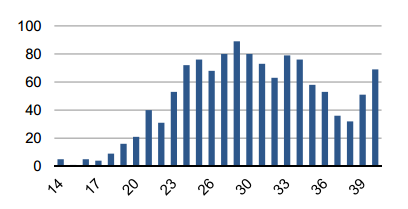
Figure 5 - Frequency distribution of 0201 CAN id
"As long as you're sitting on the network, detecting these things is so easy and you can shut them down … You know what the car should be doing. It's always spitting out information," said Valasek, director of security intelligence at IOActive.
For example, the detection of an unusually large number of packets could trigger an alert, the same if diagnostic packets contain information out of normal pattern are identified.
The economic crisis and tiny margins for vehicle manufacturers represented the principal obstacle to the introduction of security features that are considered an additional cost to cut.
"Auto manufacturers don't like adding complexity to their cars … If you're trying to tell them to change the architecture, you'd get massive push-back," declared Valasek after the presentation made by Miller at the Kaspersky Security Analyst Summit.
Despite that the topic has been discussed for a long time in the hacking community, there has not yet been documented any initiative of car manufacturers to implement security measures to prevent car hacking.
"We have no idea what they're doing. They could be building something … But it could be years down the line … Automobiles have been designed with safety in mind. However, you cannot have safety without security," Miller said.
The cases we have analyzed are spontaneous initiatives of hackers that decided to demonstrate the weaknesses of automotive industries. It is expected that in the future, security will be a fundamental requirement for our cars.
Probably we will update the firewall, or the antivirus, in our cars in real time before we even turn them on.
References
http://securityaffairs.co/wordpress/15569/hacking/car-hacking-cinematographic-fiction-reality.html
http://securityaffairs.co/wordpress/22070/hacking/can-hacking-tools.html
http://illmatics.com/car_hacking.pdf
http://usblog.kaspersky.com/podcast-protecting-cars-with-av-style-detection/
http://threatpost.com/detecting-car-hacks/104190
Learn ICS/SCADA Security